Trusting a Self-Signed or Local Issuer Certificate in Azure App Service
In some scenarios, particularly when working with development or internal applications, you may encounter issues with untrusted certificates in your Azure App Service. This guide will walk you through the process of trusting a self-signed certificate or a certificate from a local issuer, which can be critical for ensuring secure communication with services that rely on non-public certificates.
In this example, we’ll use the site https://badssl.com, a known untrusted certificate, to demonstrate the process. The steps outlined work in both App Service Environments (ASE) and non-ASE deployments. However, it is important to note that in a public App Service, certificates cannot be installed into the worker. Therefore, you will need to pull the certificate in code to trust it.
Preliminary Testing
Before making any changes, it’s useful to test the current behavior of your app when connecting to a website with an untrusted certificate. You can do this by running the following command, which will return an error if the worker does not trust the endpoint:
curl https://self-signed.badssl.com/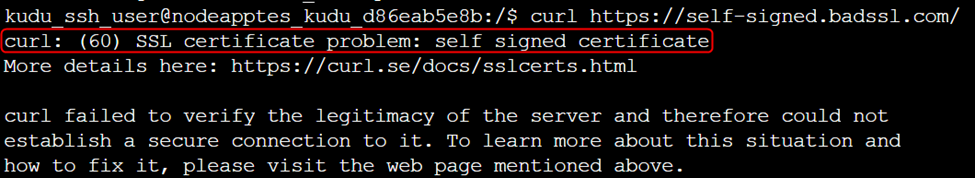
Steps to Trust the Certificate
Step 1: Access the Kudu Console
Navigate to the Kudu console of your app by going to Advanced Tools > Go > and selecting either the CMD or Bash option, depending on whether your app is running on Windows or Linux.

Step 2: Download the Certificate
To download the certificate that the endpoint is using, run the following command:
openssl s_client -showcerts -connect self-signed.badssl.com:443 > badssl_cert.pemThis will generate a file named badssl_cert.pem, containing the certificate.
Step 3: Confirm the Certificate
Next, confirm that the downloaded certificate resolves the trust issue. Run the following command to verify the connection:
curl --cacert badssl_cert.pem https://self-signed.badssl.com/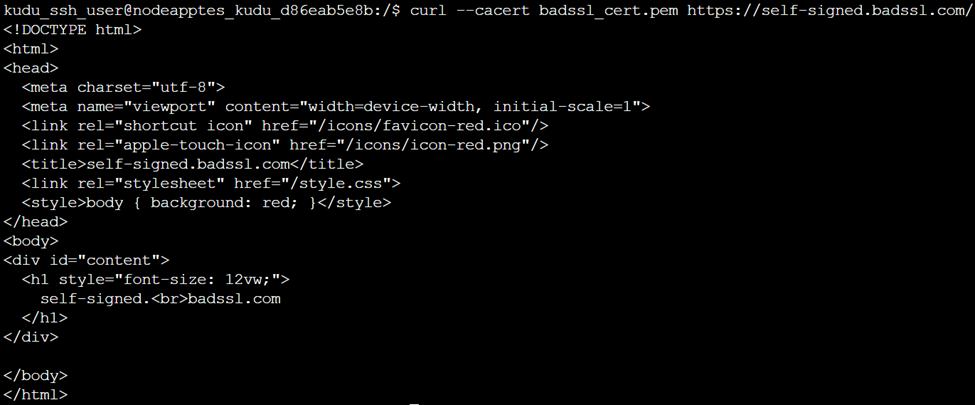
If this call succeeds without a certificate error, the downloaded certificate is correct and can be used to address the trust issue.
Step 4: Convert the Certificate
We now need to convert the .pem certificate into a format that can be uploaded to the Azure portal. Use the following command to generate a .cer file:
openssl x509 -outform DER -in badssl_cert.pem -out badssl_cert.cer
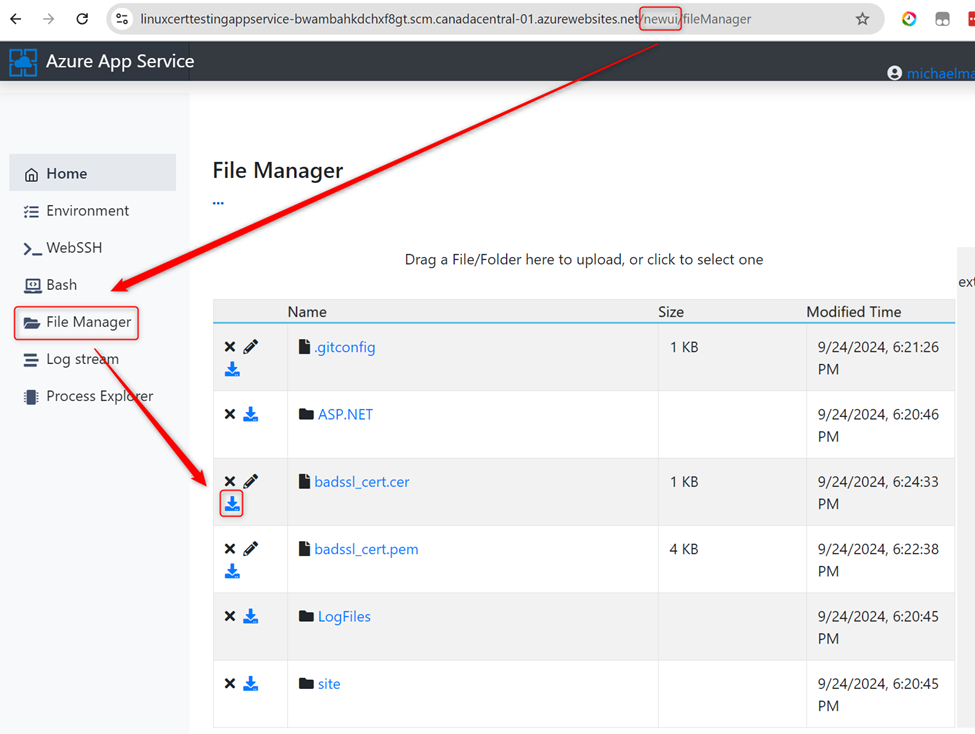
Step 5: Download the .cer File
For Windows App Service, you can use the file browser to download the .cer file. If you’re using Linux, you can access the file browser by adding “newui” to the URI of the Kudu console.
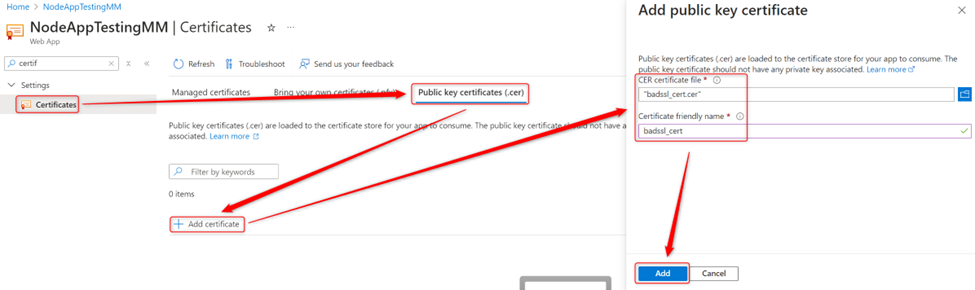
Step 6: Upload the Certificate to the Azure Portal
To upload the public certificate to your Azure App Service:
- Navigate to your app in the Azure portal.
- Go to Certificates > Public Key Certificates (.cer) > Add Certificate.
- Upload the
.cerfile you downloaded.
Once uploaded, the certificate’s thumbprint will be available, which might be needed later for configuration.
Step 7: Load the Certificate into Your App
There are several ways to load the certificate into your app, depending on your environment:
Step 7a: In an App Service Environment (ASE)
Use the app setting WEBSITE_LOAD_ROOT_CERTIFICATES, which supports comma-separated thumbprint values but does not allow the * wildcard.
- On Windows, this loads the certificate into the worker, making it trusted by all apps in the App Service Plan.
- On Linux, you will also need to load the certificate into the local cert store using a web job when the app starts.
Step 7b: In a Non-ASE Deployment
Use the app setting WEBSITE_LOAD_CERTIFICATES, which accepts either a comma-separated list of thumbprints or * to load all uploaded certificates. However, this does not add the certificate to the cert store for trust; it will simply make the certificate available to your code for use.
Example to use the certificate in code
Load certificate in Windows apps
Example to load the certificate in a container’s cert store
Load certificate in Linux/Windows containers
Step 7c: For Linux Node.js Workers
Use the app setting NODE_EXTRA_CA_CERTS to point to /var/ssl/certs/<Thumbprint>.der, which uploads the certificate to the local Node.js keystore for trusted communication.
Conclusion
By following these steps, you can successfully trust self-signed or local issuer certificates in Azure App Service, ensuring secure connections for your applications. Whether you’re operating in an ASE or a non-ASE environment, these methods allow you to establish certificate trust in a flexible and scalable manner.


