How to setup Authentication (Easy Auth) using Entra in Azure App Services
Prerequisites
- An Azure App Service (Web/Function App)
- An Azure Entra Tenant
- An Azure Entra App Registration
This is the Source documentation we will be following. If things change I would look to this for guidance.
Configure your App Service or Azure Functions app to use Microsoft Entra sign-in
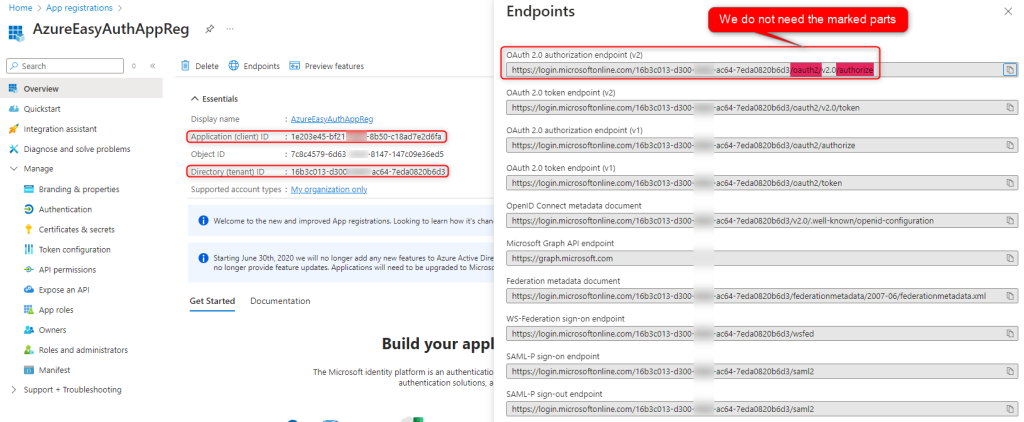
Setting Up the App Registration
Record the following information ‘Application (Client) ID’, the ‘Directory (tenant) ID’, and the ‘Oauth 2.0’ Endpoint.
For the endpoint we will edit it down to the following format.
<authentication-endpoint>/<tenant-id>/v2.0
https://login.microsoftonline.com/16b3c013-d300-____-ac64-7eda0820b6d3/v2.0
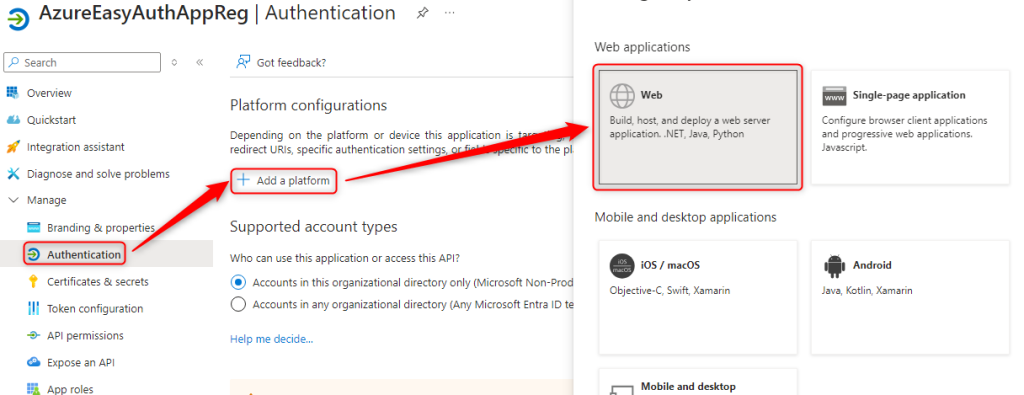
Next we will move to Authentication > Add a platform > Web
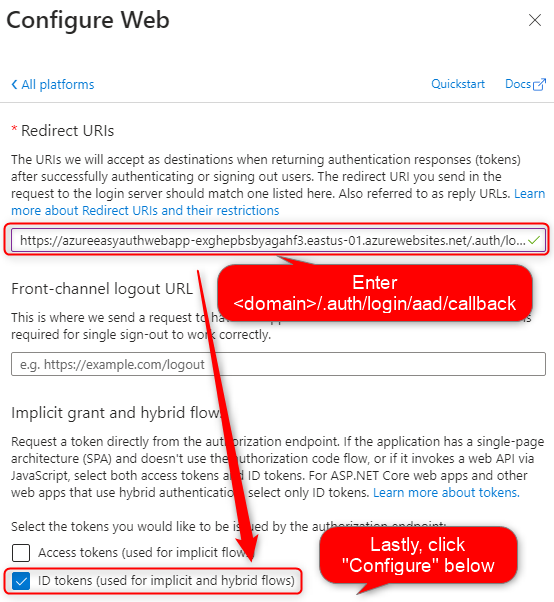
You will enter the domain of your app with an AAD callback URI at the end and click “Configure”.
“https://<AppName>.azurewebsites.net/.auth/login/aad/callback“
Here is an example of my apps domain for reference.
Note: I’m using the new beta app naming scheme. The old one also works ‘https://<AppName>.azurewebsites.net/.‘
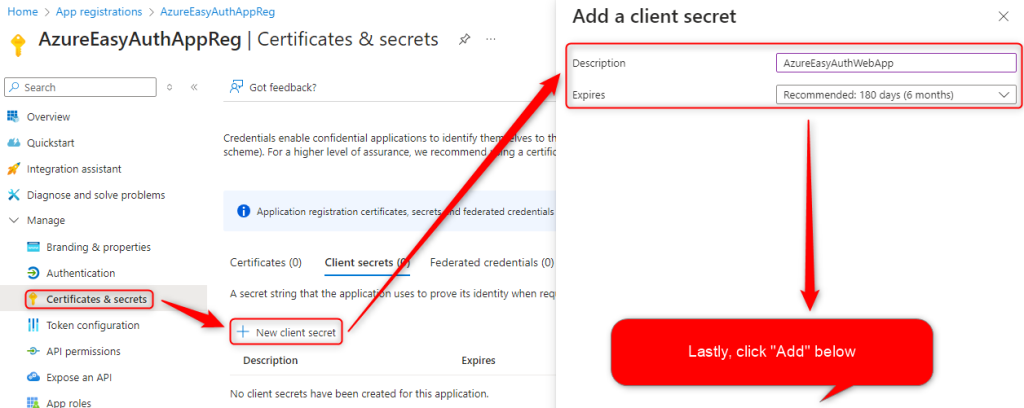
Next we will make a secret
Go to Certificates & secrets > New Client Secret > Add a Description > Click Add.
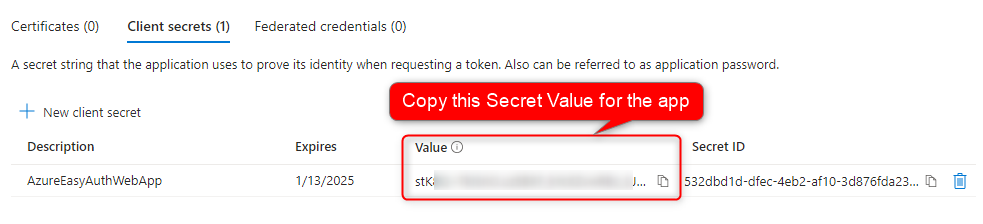
Copy down the secret value after creating the secret for later.
Lastly we will configure the App Registration API permissions.
Expose an API > Add > Save
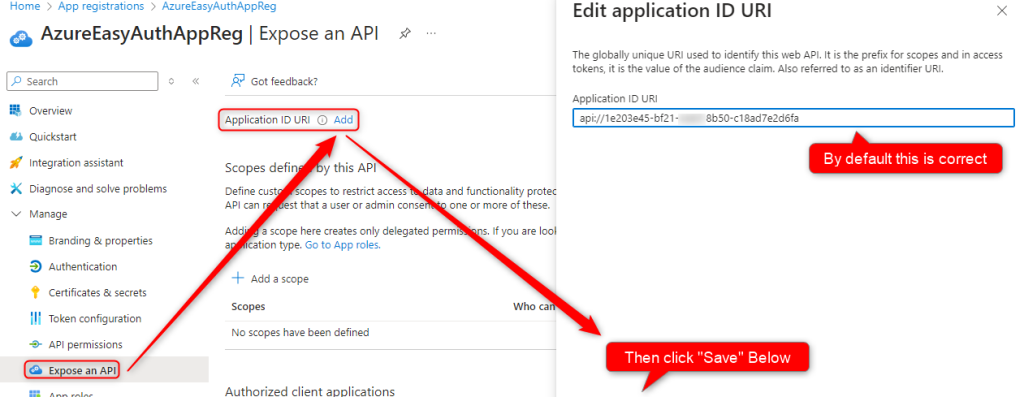
Note down the Scope URI for the app.
Add a scope > Add ‘user_impersonation’ > Admin and Users > and add the display and description > Click Add Scope
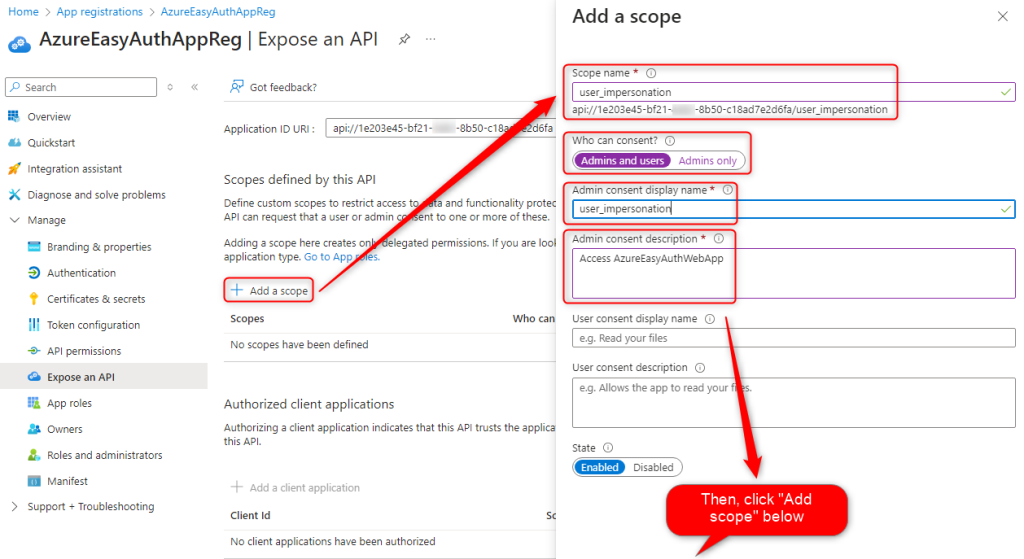
Setting Up the App
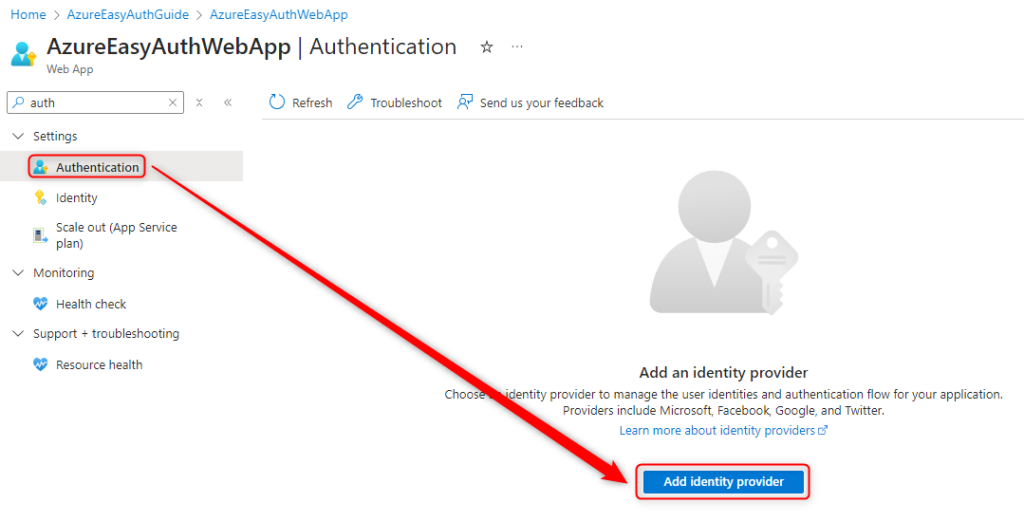
Open the app in the portal > Authentication > Add identity provider
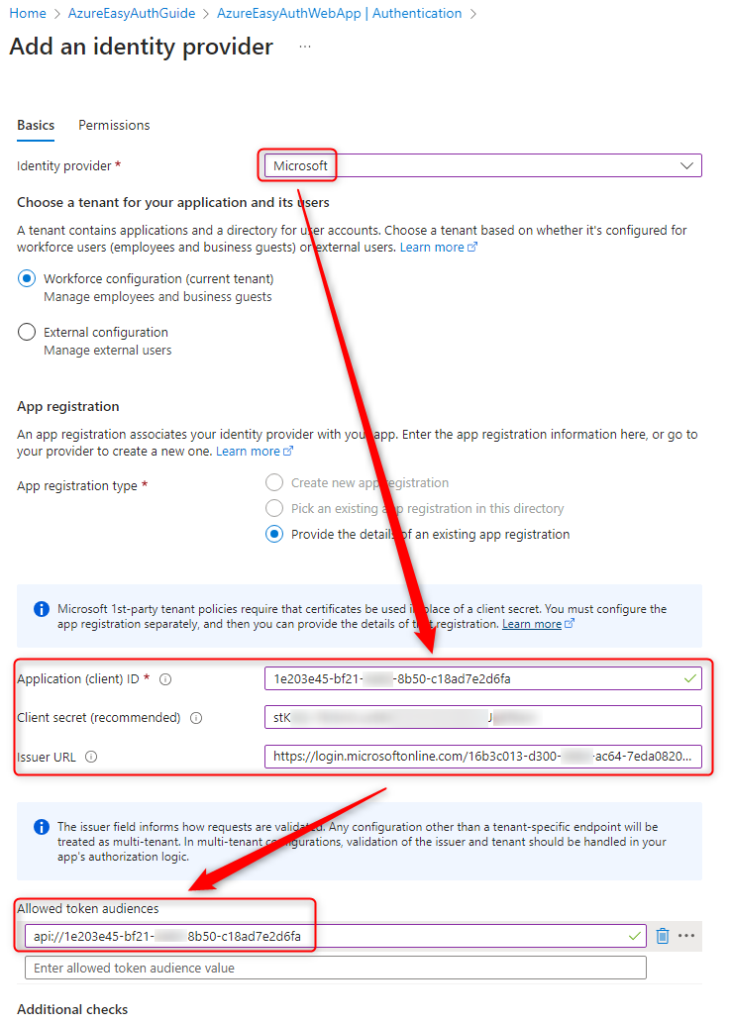
Choose ‘Microsoft’ and fill out the form.
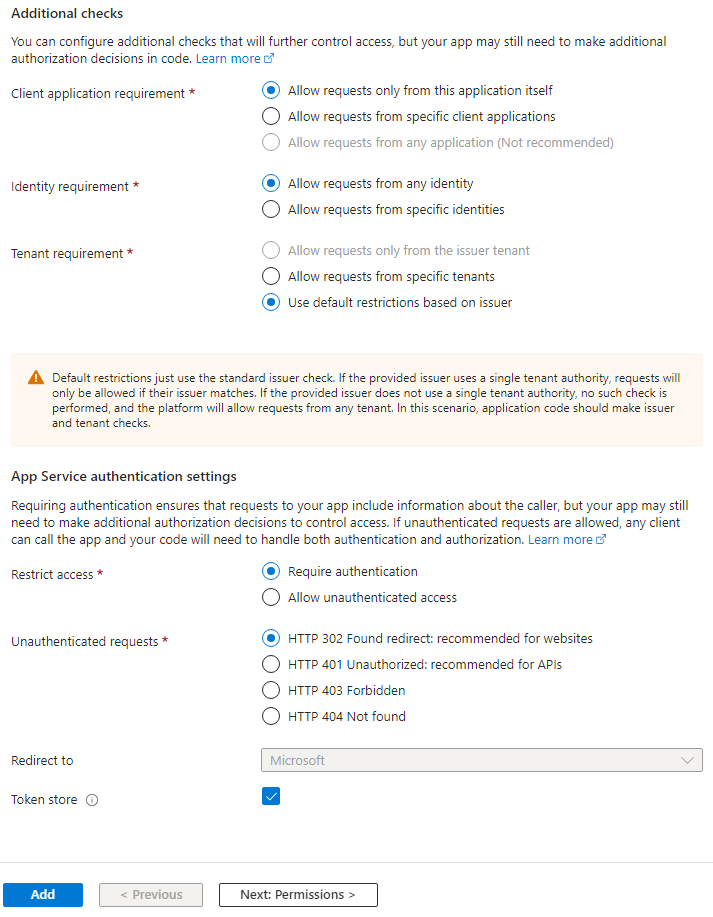
The rest of this can be left as default shown below.
Validating It worked
At this point you should be able to browse your app’s domain and the first login should ask for permission to access the app.
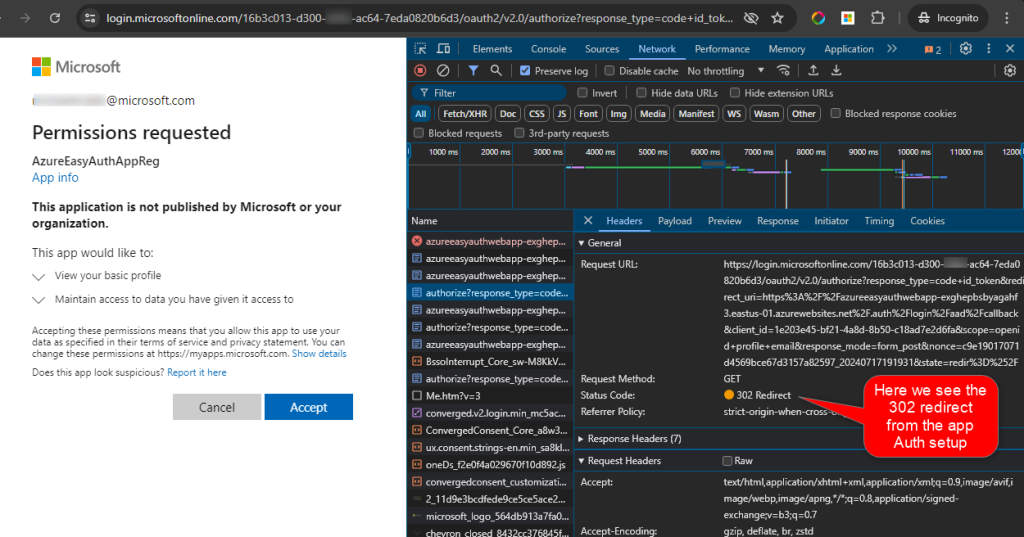
From this point on you should be able to access your app without issues.