Azure App Services Authentication – OpenID Connect Configuration Error

Issue Summary
When configuring Authentication (Easy Auth) on an Azure App Service, we encountered the following error:
500 Unable to download OpenID Connect Configuration
This error prevented the authentication module from initializing correctly.
Root Cause
The error stemmed from a failed TLS handshake when the App Service attempted to reach the specified OpenID Connect issuer endpoint.
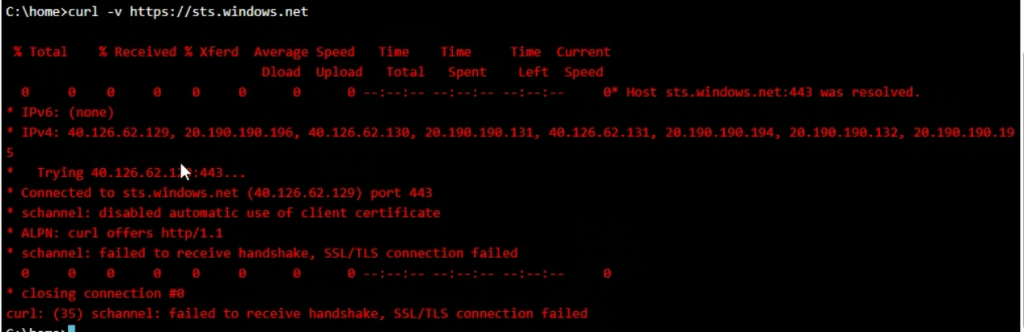
Investigation Steps:
- Accessed the App Service’s Kudu Console via the Advanced Tools blade in the Azure portal.
- Used
curl -vto test connectivity to the issuer endpoint defined in the Authentication blade.curl -v https://sts.windows.net
Findings:
- The endpoint
https://sts.windows.netreturned a TLS handshake error. - The failure was likely caused by a firewall or network security device performing TLS inspection/decryption, which broke the certificate chain and prevented secure communication.
- There are 2 primary endpoints for Microsoft authentication so you may be able to use
https://login.microsoftonline.comto mitigate this issue.
Resolution
To restore authentication functionality:
- Switched the issuer endpoint in the Authentication configuration to
https://login.microsoftonline.com - Or allow the connection through the firewall which is doing TLS decryption and breaking the handshake.
Key Takeaways
- The App Service Authentication container must be able to securely connect to the OpenID Connect issuer endpoint.
- TLS inspection or SSL-breaking middleware (e.g., corporate firewalls, proxies) can disrupt secure connections and cause configuration errors.
- Always verify endpoint accessibility using
curl -vor similar tools in the Kudu Console when troubleshooting.


